The Wikileaks Party in Australia is officially on the ballot in elections due to be held by November 30 this year. Wikileaks’ founder and its most famous personality, Julian Assange, will run for the Senate in the state of Victoria. On Thursday July 25 2013 they announced their slate of candidates, only to immediately suffer a DDOS attack for which US hacker @th3j35t3r claimed responsibility.
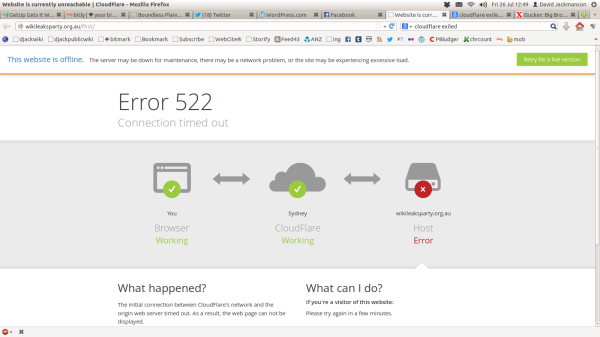
On July 26 the Wikileaks Party website was still down. An error message was provided by Cloudflare , a company which assists websites in surviving attacks by monitoring their traffic, detecting hostile activity and blocking that activity before it stops the original website working:
Cloudflare is already credited with protecting the main Wikileaks website from a DDOS attack in August last year. However, Cloudflare has a more sinister side, one that should give anyone connected with Wikileaks second thoughts about trusting any private information to it, and that knowledge has been public since 2011 thanks to Yasha Levine writing in The Exiled. Cloudflare founder Matthew Prince has a long history of working directly with US law enforcement, since he managed the anti-spam Project Honey Pot in 2003:
“Mr. Prince has…focused effort on providing enforcement officials with the necessary information and tools to prosecute violators of the federal CAN-SPAM Act and other anti-spam laws. To that end, Mr. Prince managed the development of Project Honey Pot, an Unspam community-service project that consists of a distributed system of decoy e-mail addresses that website administrators can include on their sites in order to gather information about the robots and spiders that spammers use”
So Prince happily says he has already started one company to work directly with US Federal law enforcement. His current project, Cloudflare is potentially even closer to the national security apparatus:
“We ran [Project Honey Pot] as a hobby and didn’t think much about it until, in 2008, the Department of Homeland Security called and said, “Do you have any idea how valuable the data you have is?” That started us thinking about how we could effectively deploy the data from Project Honey Pot, as well as other sources, in order to protect websites online. That turned into the initial impetus for CloudFlare”.
So, while the Wikileaks Party says it will be “fearless in its opposition to the creeping surveillance state, driven by globalised data collection and spying agencies”, and says it supports protection for whistleblowers, the Party is funnelling all traffic to its website through computers belonging to a company with close and friendly links to that very same surveillance state. This could give the US government very easy access to the IP address of all visitors to the Wikileaks Party website. How could this hurt Wikileaks supporters?
Well for example, one day Wikileaks may well release official Australian information that is embarrassing to the the US government. If the US Government had already issued a National Security Letter to Cloudflare telling it to retain details of which IP addresses visited the Wikileaks Party site, they could look at those records and see if anyone had visited the Wikileaks Party website from a government computer, or if an unusual or new pattern of visits had been logged in the time before the leak. If anything looked promising, for instance if many visits were logged from an Internet cafe that had never accessed the website before, that may well narrow the search for the leaker down a lot. Comparing records of visitors to both the Wikileaks’ Party website and the main Wikileaks website could make it yet easier to track down a would-be-anonymous leaker. These sort of techniques are how General David Petraeus’ lover was tracked down last year after she sent threatening emails from anonymous addresses connected to hotel Wi-Fi networks last year.
If we take Cloudflare’s assurances at face value, however, we have nothing to worry about. They tell us “If the NSA is listening in on any transactions traversing our network, they are not doing so with our blessing, consent, or knowledge“, and in the same post on the company blog they go into some detail about how SSL is used to encrypt traffic on Cloudflare, and why they think it is unlikely that the NSA is able to break Cloudflare’s 2048-bit encryption. Which is a lovely story to tell children at bedtime, but utterly irrelevant to your online privacy. What SSL does is encrypts your messages. So if you sent me an email saying “Let’s go to the pub tonight”, and I sent you an email back saying “Great!”, then an online snooper wouldn’t be able to read the contents of our messages. But what they could know is that you had sent me a short email, and that I had sent you a short email in reply. If that snooper already knew that the two of us often go to the pub, and that we usually arrange our drinking by email, it’s pretty easy to work out, without breaking any encryption, where she could snoop on us that evening. This is described in much more detail in a paper by Shuo Chen, Rui Wang, Xiao Feng Wang and Kehuan Zhang (pdf file):
“Specifically, we found that surprisingly detailed sensitive information is being leaked out from a number of high-profile, top-of-the-line web applications in healthcare, taxation, investment and web search: an eavesdropper can infer the illnesses/medications/surgeries of the user, her family income and investment secrets, despite HTTPS protection; a stranger on the street can glean enterprise employees’ web search queries, despite WPA/WPA2 Wi-Fi encryption”.
So the NSA may not be “listening in”. But they don’t have to listen in, as such, to find out a lot about you.
What has Cloudflare already provided the US government? We can get some idea by looking at another part of that Cloudflare blog post:
“To date, CloudFlare has never received an order from the Foreign Intelligence Surveillance Act (FISA) court…As a policy, we challenge any orders that have not been reviewed and approved by a court. As part of these challenges, we always request the right to disclose at least the fact that we received such an order but we are not always granted that request…CloudFlare fully supports the calls for transparency today by other web companies like Google, Microsoft, and Facebook. At a minimum, we request the law be updated to allow companies to disclose the number of FISA orders and National Security Letters (NSLs) they have received”.
So Cloudflare mentions orders from the secret FISA court, and National Security Letters. They deny that they’ve ever received FISA orders, but don’t deny receiving any National Security Letters. So we can infer that they have received NSLs, and that they have complied with them. In their security policy they say:
“It is possible that CloudFlare may be required by court order to provide information about our customers. CloudFlare may also be required to provide information pursuant to law, applicable regulation, subpoena or other legal process”.
Which once again implies that while they may challenge orders that are not issued by a court, in the end they are willing to comply with US Government orders for information.
When I asked the Wikileaks Party on Twitter why they were using Cloudflare, I was answered by their Chief Technology Officer who apparently chooses to be known online only as @karwalski. Karwalski said that Cloudflare was keeping the site online despite the attack. When I asked why Wikileaks was funnelling information through servers of an organisation closely linked to the national security state, karwalksi asked if I had an alternative suggestion. I responded that it wasn’t my job to help Wikileaks do it’s job of protecting the privacy of visitors to its site (19), and was told:
“Ok, you had better not ever be a passenger or driver of a car, they are dangerous. Cool logic dude“.
So that’s what the Wikileaks Party in Australia thinks of your privacy. If you’re ever thinking of leaking anything to anyone, don’t let it be to Wikileaks – you can’t trust them with your online security.
—-
UPDATE:
After a week of me calling out the Wikileaks Party by name on Twitter about the privacy risks with their website, Assange’s running-mate in Victoria, Leslie Cannold, finally decided to respond tonight (Monday August 12 2013), when Twitter user @BenHarkin asked her about it:
It’s not my area of control or expertise. If tone were different I would have referred it. But rude irks me. @benharkin @djackmanson
So, there’s some handy information. If you want to hold the Wikileaks Party accountable for anything bad they might be doing, remember that you have to ask nicely, or they don’t have to worry about it.
UPDATE TWO:
Cannold thinks my rude, aggressive, presumptious tone should insulate the WikiLeaks Party from answering questions about the security risk its website poses to visitors:
U r outrageously rude & entitled. I wouldn’t dream of following yr barked orders in real life & won’t online. @djackmanson @benharkin
I thought Wikileaks was all about aggressive journalists demanding answers and accountability from the powerful?

[…] go wrong. The second is even more interesting. Even if she refuses to answer my questions about why the Wikileaks Party makes it easy for the US Government to spy on visitors to its website, maybe Leslie Cannold would turn out to be a good Senator. Maybe – and I realise that […]